Applications
Legacy applications benefit from OCALA in two different ways. Firstly, OCALA enables applications to leverage the new functionality offered by overlays. Secondly, the OC-I sub-layer of OCALA allows a path to traverse multiple overlays thus composing their functionalities. We now describe some applications that demonstrate these two types of benefits.
Functionality Enabled by Overlays
i3 offers functionality such as NAT traversal and receiver imposed middleboxes, while HIP offers secure mobility. The following applications leverage these through the i3 and HIP OC-D modules.
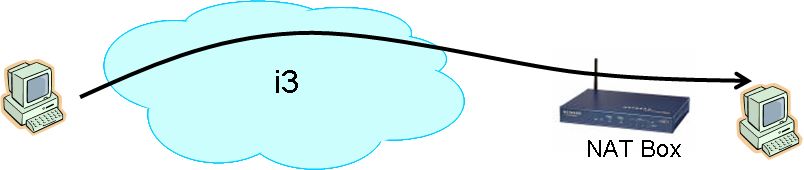
- NAT Traversal: i3 enables access to machines behind NATs. By
using the i3 OC-D module in conjunction with the OC-I sub-layer, a user
can run legacy servers behind NATs. In addition to allowing external
users to contact these servers, it also enables home users to securely
access their machines from anywhere by simply remembering the
human-readable name of their home machine.
For a demo of a web server accessed over i3, using the OCALA remote-client-proxy, please visit http://www.cs.berkeley.edu/~dilip/photos.shtml.
For more details on the NAT traversal service offered by OCALA, please visit the OCALA NAT Traversal Service page.
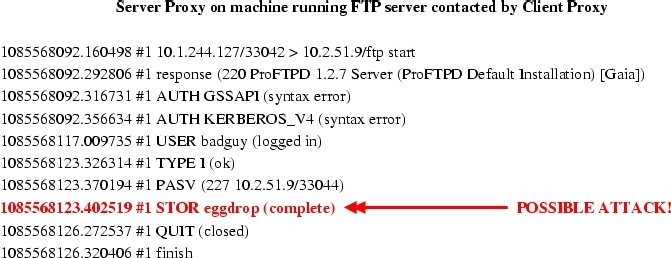
- Receiver Imposed Middleboxes: i3 enables hosts to redirect all
incoming traffic to go through a middle-box which may be located
anywhere in the network. This functionality of i3 can be used to
force all incoming traffic to a legacy server to pass through an
intrusion detection middlebox, which may not be located on the physical path to
the server. The following figure shows some analysis performed by a Bro intrusion
detection box imposed on the path to a legacy FTP server using OCALA.
- Secure Mobility: HIP enables hosts to securely communicate with each other even when the hosts are mobile. This functionality of HIP is leveraged to support ssh connections that remain alive even when one of the hosts changes its IP address.
Functionality Enabled by the OC-I Sub-layer
The OC-I sub-layer's ability to provide simultaneous access to multiple overlays and to bridge together different overlays enables the following applications:
- Secure Intranet Access: A more flexible and
secure version of Virtual Private Networks (VPNs) can be implemented by using
the OC-I sub-layer to contact legacy hosts over a overlay. A legacy
server gateway runs inside the organization and hence has unrestricted
access to all intranet hosts. To access Intranet machines, external
end-hosts relay packets through the legacy gateway. Authentication
and encryption are important requirements in this scenario, and we
simply leverage the OC-I sub-layer's security mechanisms for this
purpose. Any routing overlay, including vanilla IP, can be used for
communicating between the user's machine and the legacy gateway. The
main advantage of this system over regular VPN-based systems is that a client
can access multiple Intranets at the same time even if both Intranets
use the same address range. Users specify their preference through
the configuration file -- for example, all connections to
*.company1.com should go through the gateway1 of company 1
while connections to *.company2.com should use the gateway of
company 2. Another distinguishing feature of this system is that,
unlike in traditional VPNs, a client is not assigned an IP address
from the Intranet address space. This improves security
by making it difficult for a client infected by a scanning worm
to directly attack other hosts within the Intranet.
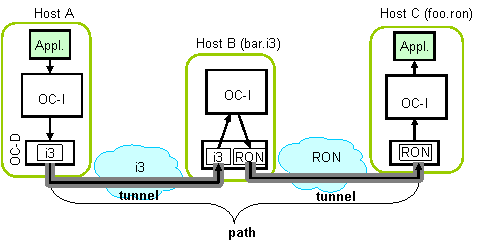
- Overlay Composition: Overlay composition allows an application
to explicitly stitch together different network overlays. Apart from
enabling inter-operability, this allows a user to merge the
functionalities of multiple overlays in interesting ways. For
example, a user who connects to the Internet through a wireless hop,
may use i3 for uninterrupted communication while switching between
various wireless networks. In addition, the user may also wish to
optimize wide-area performance using RON. We achieve this by using
i3 to connect to a close-by i3-to-RON gateway, which will then relay
packets over a RON-optimized path.