Receiver Imposed Middleboxes
i3 enables hosts to redirect all incoming traffic to go through a middle-box which may be located anywhere in the network. This functionality of i3 can be used to force all incoming traffic to a legacy server to pass through an intrusion detection middlebox, which may not be located on the physical path to the server.
We have set up a webserver on a machine named dilip-secure.pli3. All traffic to dilip-secure.pli3 is forced through a Bro intrusion detection system running on a machine not on the physical path to dilip-secure.pli3. The following diagram illustrates the scenario.
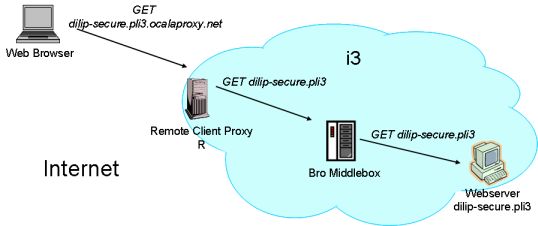
Click here to attack dilip-secure.pli3 by trying to fetch /etc/passwd. A new browser window will open - You will not be able to access the file ofcourse :-).
Your attack will be recorded in the Bro Monitoring Page.